
In recent years, the issue of young lawyers' growth has drawn significant attention from the outside world, with the career development of young criminal defense attorneys emerging as a particularly challenging and critical area within the legal industry. From August 24 to 25, the highly anticipated 2024 National Forum for Young Criminal Defense Lawyers, accompanied by a specialized training camp, was grandly held at the Millennium Hotel in Beijing. The event was jointly organized by Beijing Kyoto Law Firm and the "Jing" Ying Club, a professional network dedicated to nurturing young lawyers under the KyotoKING brand. As one of the rare domestic forums focused exclusively on the niche field of young criminal defense practitioners, the forum brought together over 200 young lawyers from more than 16 provinces across China. Together, they delved into the professional growth of young criminal defense attorneys, exploring how to enhance their expertise and influence in today’s evolving legal landscape. Participants also engaged in in-depth discussions on defense strategies for cybercrime cases and plea bargain proceedings, while examining the potential of artificial intelligence to expand opportunities and reshape the practice of criminal defense for younger lawyers—offering fresh, cutting-edge perspectives on this specialized area of law.
This article is Liu Pinxin, Professor at the Law School of Renmin University of China Posts from the forum, compiled and published for readers' enjoyment.

Liu Pinxin, Professor at the Law School of Renmin University of China
Thank you to Kyoto Law Firm, and thank you to the Young Criminal Defense Lawyers Forum for the invitation!
Today, my presentation is titled "An Innocence Defense Based on Digital Evidence." The main focus will be on how to mount a successful defense of innocence—specifically in cases where the defendant has already pleaded guilty and agreed to a plea bargain—by leveraging electronic evidence. There are several key considerations behind this topic. Importantly, over the past two years, I’ve led my team through two landmark innocence defense cases, both of which ended in complete success: the defendants were acquitted despite having previously admitted guilt and accepted the plea deal. What’s more, the strategies we employed for these cases differed significantly from our usual approach—this serves as the backdrop to today’s discussion.
Beyond this context, there’s a crucial reason: an acquittal is the crown of criminal defense. I know many criminal defense lawyers spend their entire careers striving to achieve a successful not-guilty verdict.
The second context is that I’ve consistently argued that electronic evidence defense represents a rising star in criminal defense—it’s a type of defense rooted in one of the eight recognized categories of evidence. This approach relies heavily on vast amounts of data, setting it apart from traditional forms of evidence presentation. Electronic evidence defense isn’t just a novel method of challenging evidence; it goes beyond merely addressing the three key attributes of electronic evidence—legality, authenticity, and relevance. Instead, it also introduces substantive defenses, such as determining guilt or innocence and distinguishing between different charges. Moreover, it ushers in shifts in procedural strategies and gives rise to entirely new defensive tactics, ultimately impacting every facet of legal representation.
More importantly, based on my practical experience—and also from an academic perspective—I’ve discovered that defending with electronic evidence is a particularly compelling and enticing path. In fact, I’ve presented this topic over ten times now, each time focusing on a slightly different case, constantly inspiring the team to push the boundaries of innovation. Considering these three key aspects, today I’m introducing our topic: "Acquittal Defense Through Electronic Evidence."
Now, let’s consider the fundamental principles behind a defense of innocence based on electronic evidence. I’ll start by offering a straightforward analysis from a conceptual perspective. First of all, a defense of innocence can be quite complex and, at times, highly controversial. It can be defined as a strategy aimed at disproving the charges brought forth by the prosecution. Moreover, the concept of "electronic evidence defense" is one that shouldn’t be interpreted literally. When I’ve asked numerous lawyers about this, nearly all of them initially assumed it simply involves defending against accusations related to electronic evidence—or perhaps reducing it solely to general evidence defense. However, as my paper clearly demonstrates, this type of defense goes far beyond merely challenging the admissibility or authenticity of electronic evidence. Instead, it emphasizes using electronic evidence itself as a strategic tool in legal arguments. In essence, electronic evidence can serve as a versatile instrument for mounting any kind of legal defense. Additionally, in the context of cybercrime research, there’s growing emphasis on rethinking how we approach defenses—whether by shifting our focus back to physical spaces or, increasingly, pivoting toward the digital realm. From this perspective, the very definition of "electronic evidence defense" remains relatively novel and evolving.
When these two terms are combined, the types of acquittal defenses based on electronic evidence are numerous, including defenses for wrongful convictions, mistaken convictions, and fabricated cases. A defense for a wrongful conviction involves the suspect claiming they didn’t commit the crime—essentially, that law enforcement authorities wrongly accused them. In contrast, a defense for a mistaken conviction argues that the investigative authorities objectively misidentified the facts. Beyond these two scenarios, there’s also a significant category known as "fabricated case defense," where certain information or data companies—often collaborating with police or prosecution agencies—are driven by commercial interests. These companies deliberately uncover or even create misleading leads to pressure law enforcement into initiating investigations, ultimately helping to engineer cases out of thin air.
If judicial authorities fail to detect these deliberately fabricated cases—or, even if they do spot them, choose not to correct them—they end up undermining the very integrity of the judiciary, leading to the phenomenon of case fabrication. By approaching this issue from this angle, we can uncover a fresh avenue for acquittal defense: specifically, can you clearly identify during your defense which companies or individuals were secretly orchestrating the fabrication? If you bring this critical information into the courtroom, it could effectively shift the narrative—and that, in turn, may pave the way for an acquittal. This is one promising angle to explore.
The second angle is from the perspective of procedural law— even in cases involving guilty pleas and plea bargains, defendants can still mount an acquittal defense based on electronic evidence. Some individuals may have pleaded guilty or accepted a plea without fully understanding the implications, so once they gain clarity on the specifics of the electronic evidence, they may indeed have the opportunity to argue for their innocence using that very evidence.
Here’s an example I’d like to share—one of the two wrongful conviction cases my team and I worked on. It involves a charge under the crime of illegally obtaining data from a computer information system. Simply put, a company was accused of using web crawlers or various other methods to harvest video resources belonging to the victimized company, thereby gaining unauthorized commercial benefits. This behavior could potentially be classified as either copyright infringement or, more specifically in this case, the crime of illegally obtaining data from a computer information system. As indicted here, the charge is for illegally obtaining data from a computer information system.
The key evidence in this case comes from the investigative actions taken by public security authorities at the office of the company involved, where they conducted a site inspection and examination. This resulted in the preparation of a detailed on-site inspection report, which revealed traces of the "crawler" software on employees' company-issued computers—specifically, the actual data collected by the crawler. This allowed investigators to determine exactly how much data had been "scraped" and to understand the method used to carry out the scraping activity. The second critical piece of evidence is the electronic data itself, but even more significant is the forensic analysis report generated from this digital evidence. The report not only identified the alleged "crawler" account but also provided a precise count of the data records extracted by the malicious software. Finally, there’s an invoice that documents the cost incurred by the victimized company after its system was compromised. The company hired a technical firm to conduct a thorough system audit, and the fee for this service—10,700 yuan—directly corresponds to the amount of financial loss suffered, thereby meeting the legal threshold required to initiate criminal proceedings.
At the time, public security authorities investigated two separate cases—first, they examined this company, and second, they looked into another company based in Nanjing. That Nanjing-based firm had employed the same questionable practices, though the only difference in evidence was that the loss amount at the latter company totaled 10,500 yuan. Notably, the case involving the Nanjing company has already resulted in a guilty verdict, and several key individuals from that case have already pleaded guilty and agreed to accept punishment. Following their plea and agreement, all of them were released on bail pending further legal proceedings. These individuals include the company’s general manager and senior executives, both of whom are highly accomplished graduates of the prestigious "Youth Classes" at University of Science and Technology of China and Tsinghua University—they’re ambitious leaders with big plans for the future. However, these executives soon realized that even if they managed to secure a suspended sentence, it could still pose significant challenges for their upcoming entrepreneurial ventures or overseas opportunities. Moreover, they worried that such a conviction might also affect their children’s futures. Given this situation, they began considering whether they could mount a defense arguing for not guilty. I suggested they explore an alternative approach: focusing on the electronic evidence. Specifically, I pointed out that the electronic data collected by the investigating authorities appeared problematic—while the authorities claimed the data was obtained directly from your company, there were clear inconsistencies that raised serious doubts about its authenticity and reliability.
To demonstrate that the crawler identification was invalid, the expert report noted it relied on UV tools to analyze crawler data—but my aim was to prove that these crawler records weren’t exclusively used by the defendant; rather, they likely included data belonging to the victim as well. For instance, when the forensic agency claimed there were 20,000 crawler entries, this didn’t necessarily confirm that all of them belonged to the defendant; it’s entirely possible that some of those records actually came from the victim. Moreover, we carefully reconstructed the forensic agency’s methodology and uncovered significant flaws. Specifically, their approach involved searching using specific keywords, which inherently led to inaccurate results. Given these critical shortcomings in their process, the prosecution later submitted an additional expert opinion during the trial. However, when I argued to the judge that the case should be dismissed outright—since the entire basis for the charges rested on false evidence—the prosecutor insisted on proceeding with the trial, refusing to withdraw the indictment directly. In response, I urged the prosecutor to call witness Wang某某 to testify. In reply, the prosecutor claimed they couldn’t locate Wang. So, I suggested instead summoning the police officer who had originally collected the evidence, as his failure to appear raised serious concerns about potential misconduct—or even dereliction of duty. When pressed further, the officer revealed he had already resigned.In light of these revelations, I urged the court to issue a detailed list of questions to the local Public Security Bureau, asking over 60 specific inquiries about the investigation. Unfortunately, the bureau largely ignored our requests, offering no substantive responses. As a result, despite the lack of cooperation from law enforcement, the case eventually moved forward. Ultimately, after months of waiting—stretching well into December 31 of the previous year—the prosecution finally agreed to withdraw the charges altogether. This decision marked the formal conclusion of the case. This case clearly underscores the significant potential—and practical viability—of mounting an acquittal defense based on electronic evidence.
This is the image for Step 17, and it shows a small icon—a symbol representing an external portable hard drive. None of the previous step images included this icon, yet suddenly, it appears in Step 17. This immediately raises suspicion. But what exactly is this portable hard drive? It turns out to be a folder located outside the defendant company’s employee’s computer. This discovery leads us to suspect that someone may have transferred files onto the employee’s computer precisely during Step 17—making this location a key piece of evidence confirming unauthorized data insertion. But how do we prove that data was indeed transferred into the system? To answer that, we need to examine the data from this specific step. Upon opening it, we find that all the file modification timestamps date back to March 14, 2019—well before the actual forensic investigation took place on March 29. In contrast, the modification times for *all other* files in the system also align with the later date of March 29. Clearly, there’s a major discrepancy here, raising serious questions about the integrity of this particular step.
After I discovered this, I called in the employee on bail and the computer user, asking them to explain how the public security authorities collected evidence from you at the time. They said there were two officers—one showed his police ID, while the other didn’t. But I pointed out that public security investigations typically involve two investigators plus a neutral witness—so shouldn’t there have been three people present? Why were only two involved? They confirmed it was just the two of them. Then I asked: "Out of those two, did only one officer show their ID?" They replied, "Only one." I pressed further: "So, was it the person without the ID who actually operated the computer?" They admitted, "Yes." This revelation immediately raised red flags, confirming that something was amiss in the evidence-gathering process. Now the critical question becomes: Which one of the two was the computer operator—and crucially, which one deliberately withheld their identity during the procedure? When we reviewed the official record, we noticed something highly unusual: There was only one witness listed—someone named Wang, whose last name we couldn’t quite recall. To our surprise, this individual turned out to be an employee of the very company that had filed the complaint! As the complainant himself, he’d come to provide evidence—but remarkably, he chose to operate the computer without identifying himself. Meanwhile, the public security authorities sent only one investigator to handle the case. To verify this, we cross-referenced the complainant’s photo with the actual investigators who conducted the evidence collection. Sure enough, the person operating the computer matched the employee from the victimized company.
I spoke with the prosecutor and said, "I’m sorry, Prosecutor, but even though they’ve agreed to plead guilty and accept the plea deal, my professional opinion as a lawyer is that they’re innocent—because this is a fabricated case, deliberately staged by none other than the very person who filed the original complaint." The prosecutor replied, "Could that really be true? It’s highly unlikely. We’ll need to verify the details." After conducting their investigation, the prosecutor informed me, "Unfortunately, the complainant can’t appear in court." When I asked why, the prosecutor explained, "Apparently, the public security authorities have been unable to locate him."
Later, the investigating authorities located a disk retrieved from Alibaba Cloud on March 15, 2019, within the case files. This disk contained five compressed files—files whose contents were indeed present but weren’t initially used as evidence for the charges. Now, the public security agency has sent this data to an expert institute for re-examination. The latest analysis revealed additional information about certain "crawler" activities hidden within the files. As a result, the data has been extracted and reprocessed once again. Here’s the critical issue: To mount a not-guilty defense, it’s essential to verify whether the five compressed file packages on the disk are intact and unaltered. I’ve noticed that one of these files was created on April 19, 2019, while the other four date back to March 15. Given this discrepancy, the question arises: Which specific file did the forensic experts analyze during their re-examination? If it was indeed the April 19 file—and not one of the March 15 ones—then there’s clear evidence of tampering or manipulation.
Additionally, the relevant files for this case were created on March 14th—and there were issues with both March 14th and March 15th. Given this situation, to verify the data, we checked its checksum values. However, the timestamps provided by Alibaba, whether from April 8th or April 19th, clearly don’t match the actual dates when the data was generated. There’s no way these timestamps could be correct. So, we decided to open the data directly. Upon inspection, we discovered that the verified data actually resides in a folder dated April 19th. But when we opened it up, we found that the data itself was originally created on March 14th. More surprisingly, two of the files had identical sizes—though their names differed slightly. This led us to realize that someone had even dared to tamper with the data right here. To make matters worse, after sorting through all the data, we noticed that every single file flagged as “verified” turned out to be suspicious or outright invalid.
After I mentioned this, I became firmly convinced that the evidence retrieved by the investigative authorities from Alibaba on their second visit had been tampered with—specifically, that someone swapped the data sent back by Alibaba. The public security agency requested the evidence from Alibaba, and while Alibaba did return the data, it was clearly replaced by someone else. For instance, the document issued on March 15 showed a modification timestamp of March 14—a detail that immediately raised red flags. All the newly prepared forensic analyses pointed to the same suspicious pattern. I’m absolutely certain about this claim, but now I need to convince the judge, who admittedly doesn’t fully grasp the nuances of digital forensics. So, I’ve turned to common-sense reasoning to make my case. To strengthen my argument, I asked a colleague to analyze the "Notice of Evidence Retrieval." Specifically, I wanted to understand: What exactly was being requested? According to the notice, four items were supposed to be handed over—but in reality, five were returned instead. Moreover, this particular retrieval notice stood out from others because its official seal was noticeably smaller than usual, almost like a miniature version of itself. On top of that, there was an additional sealing mechanism that matched identically to the one used in another ongoing case. Armed with these findings, I presented the evidence to the court, conclusively proving that the original data had indeed been swapped—and ultimately highlighting serious issues with the integrity of the electronic evidence itself.
To demonstrate that the crawler identification was invalid, the expert report noted it relied on UV tools to calculate crawler data—but I aimed to prove that these crawler records weren’t exclusively used by the defendant; they likely included data belonging to the victim as well. For instance, when the forensic agency claimed there were 20,000 crawler entries, this didn’t necessarily confirm they all belonged to the defendant; it’s entirely possible that some of those records actually came from the victim. Moreover, we meticulously reconstructed the forensic agency’s methodology and discovered it was fundamentally flawed. Specifically, their approach involved searching using specific keywords, which inherently led to inaccurate results. Given these critical flaws in their process, the prosecution subsequently submitted an additional expert opinion during the trial. However, when I argued to the judge that the case should be dismissed outright—since the entire basis for the charges was built on false evidence—the prosecutor insisted on proceeding with the trial, refusing to withdraw the indictment directly. I countered by urging the prosecutor to summon witness Wang某某 to testify. In response, the prosecutor claimed they couldn’t locate Wang. So, I suggested calling the police officer who had originally collected the evidence, since his failure to appear raised serious concerns about potential misconduct or even dereliction of duty. When pressed further, the officer revealed he had already resigned. In light of these revelations, I urged the court to issue a detailed list of questions to the local Public Security Bureau, asking over 60 specific inquiries about the investigation. Unfortunately, the bureau largely ignored our requests, offering no substantive responses. As a result, despite the lack of cooperation from law enforcement, the case eventually moved forward. Ultimately, after months of waiting—stretching well into December 31 of the previous year—the prosecution finally agreed to withdraw the charges altogether. This decision marked the formal conclusion of the case. This case clearly underscores the significant potential—and practical viability—of mounting an acquittal defense based on electronic evidence.
Therefore, leveraging electronic evidence to strengthen the effectiveness of a not-guilty defense has become an inevitable choice in our era. Don’t rely solely on the elements of the crime when mounting a not-guilty plea. By using electronic evidence as the cornerstone of your defense, you can pursue outcomes ranging from complete acquittal to lighter charges—and there are countless ways to achieve this. Particularly in cases involving guilty pleas and plea bargains, both of the cases I’ve handled were initially charged with guilty pleas, yet we managed to secure 100% not-guilty verdicts, which is truly exceptional.
I recommend that everyone study independently while also seeking guidance from our expert team, which will provide you with valuable advice and help review the evidence. I believe this is a key direction for us to move forward rapidly. That concludes my presentation—thank you all!
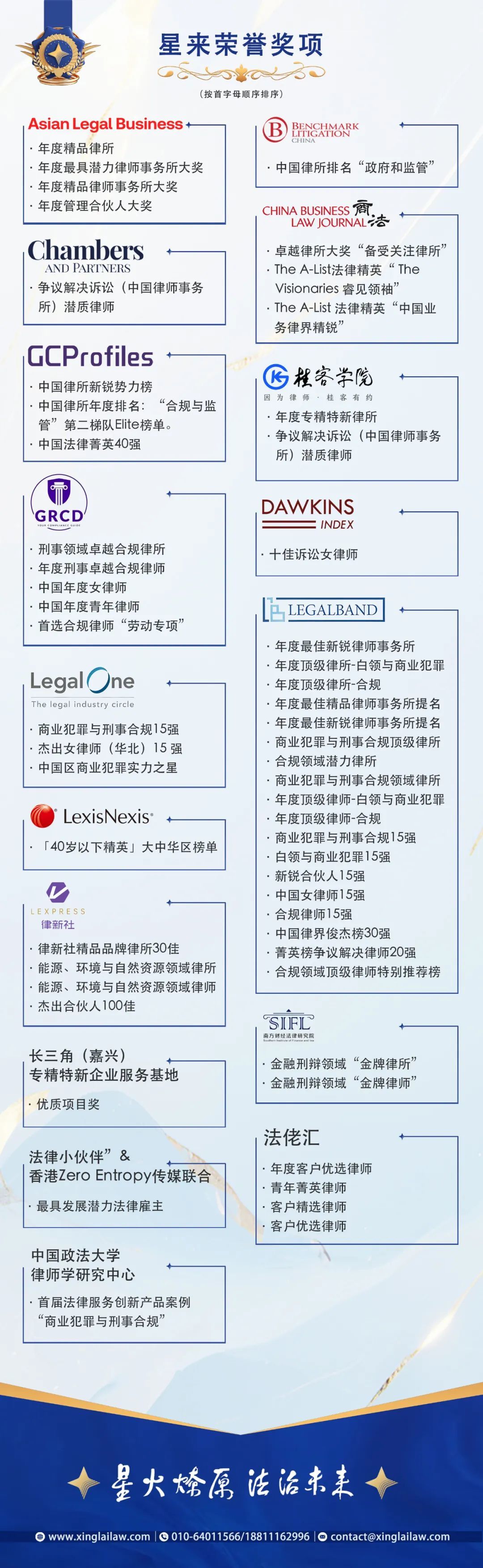
Beijing Headquarters Address: Floor 17, East Section, China Resources Building, No. 8 Jianguomen North Avenue, Dongcheng District, Beijing
Wuhan Branch Office Address: Room 1001, 10th Floor, Huangpu International Center, Jiang'an District, Wuhan City, Hubei Province
Layout: Wang Xin
Review: Management Committee

Related News


