
Specifically regarding the review process, what are some useful techniques and experiences that can be借鉴ed to prevent
This article analyzes techniques for reviewing electronic data in criminal cases. First, it clarifies exactly which "cases" contain electronic data—specifically, identifying which case files are relevant to the electronic evidence. Next, it explores how to achieve efficient, targeted reading when dealing with cases that often involve dozens or even hundreds of documents spanning multiple technical stages. Finally, the article delves into the actual review process, providing detailed insights into specific examination methods.
We would like to thank Professor Wang Ran for contributing this piece!
Tips for Reviewing Electronic Data
Introduction:
As electronics The widespread application of data in criminal cases has increasingly made the effective review of such evidence a central focus in litigation practice. Currently, when dealing with electronic data, the legal community often centers its attention on “ Data ” Itself, while regarding the accompanying data extraction and transfer “ Case file materials ” Insufficient attention has been paid. In fact, when direct access to the electronic data itself is challenging, documents such as records of electronic data, expert opinions, and lists of storage media—often found in case files—typically contain rich and valuable information. Carefully reviewing these case materials can also provide strong support for cross-examination, and in some cases, even serve as the key to breaking through the case.
However, based on current practical experience, there are still noticeable issues surrounding case files involving electronic evidence: First, What exactly are the types of electronic data? “ Roll ” , meaning that the case files and materials relevant to it often lack systematic organization; Secondly, When confronted with case files that often number in the dozens or even hundreds and span multiple technical stages, it is crucial to clearly define methods and strategies for efficient, targeted reading. Thirdly, Specifically regarding the review process, what are some useful techniques and experiences that can be借鉴ed to prevent “ Exam Grading ” Being mere formalities is a prominent challenge in current practice. This article aims to analyze and summarize around these three core issues.
1. What "tricks" are there with electronic data?
Which case files exactly correspond to electronic data? This is the first question that puzzles many legal practitioners. In fact, in criminal cases, each evidence-gathering measure related to electronic data corresponds to a specific case file—and these procedures have already been outlined in the "Supreme People's Court, Supreme People's Procuratorate, and Ministry of Public Security…" < Provisions on Several Issues Related to the Collection, Extraction, and Examination & Adjudication of Electronic Data in Criminal Cases > 》( 2016 Year, hereinafter referred to as the "Electronic Data Regulations"), and the Ministry of Public Security < Rules on Electronic Data Forensics for Criminal Case Handling by Public Security Authorities > 》( 2019 This is clearly stated in two regulatory documents, referred to below as the "Electronic Forensics Rules."
Criminal digital forensics measures include the following categories:
1. Seizure and sealing. Strictly speaking, the measure targets not the electronic data itself, but rather its "original storage media," such as mobile phones and computer hard drives. U Disks, etc. The original storage media qualify as physical evidence and are subject to relevant rules governing physical evidence, such as the exclusion of illegally obtained evidence (Article [insert article number] of the Criminal Procedure Law). 56 Articles), physical evidence verification (Interpretation of the Criminal Procedure Law, Article 86 ) and other rules that electronic data does not possess. It’s important to note that "seizure and sealing" is a priority evidence-gathering measure, essentially meaning "seize everything that can be seized." The "Regulations on Electronic Data" explicitly state: "If the original storage media can be seized, they must be seized and sealed immediately."
2. On-site extraction. Refers to directly extracting data from the device at the scene, in cases where the original storage medium cannot be easily sealed, contains volatile dynamic data (such as memory data or network transmission data), or becomes inaccessible after the device is powered off.
3. Online network extraction and remote forensic examination. The two measures target electronic data stored in online environments. The object of online extraction from the web includes "publicly released electronic data and electronic data located on remote computer information systems within China," which essentially involves downloading and securely preserving network data. Remote examination, on the other hand, is conducted "to further clarify relevant circumstances," focusing on analyzing and extracting details such as the scope of data collection, installed software, system architecture, logs, and file directory structures—commonly seen in scenarios like retrieving backend log data from cloud-based service platforms. The key distinction between the two lies in their approach: online extraction emphasizes "fixing and preserving information," while remote examination places greater emphasis on investigators' analysis, judgment, and the discovery process itself.
4. Retrieve and freeze. This is particularly applicable when electronic data is held by third parties. In the era of big data, more and more information is stored in the cloud or on remote network systems. When it’s impossible to directly seize or extract the data, the cooperation of the data holder often becomes essential. Data retrieval refers to legally requesting a third party to provide relevant information, while data freezing involves restricting public access to prevent any additions, deletions, or modifications—typically granting investigators "read-only" access only. This approach is especially useful in scenarios involving massive datasets that are difficult to extract or where there’s a risk of tampering.
5. Inspection and investigative experiments. Compared to traditional evidence, electronic data introduces an additional "examination" step in both on-site investigation and forensic analysis. This step typically involves operations such as decryption, recovery, search, simulation, comparison, and statistical analysis—tasks carried out by investigators with specialized technical expertise. Meanwhile, investigative experiments rely on simulation and reenactment techniques to determine whether electronic data can reliably reproduce a specific state or outcome under controlled conditions.
6. Inspection and Certification. To clarify the facts of the case and address specific technical issues involved, experts with specialized knowledge are assigned or hired to conduct expert assessments, or reports are commissioned from institutions designated by the Ministry of Public Security. Importantly, these individuals are not investigators but rather professional experts possessing specialized knowledge.
Case files corresponding to electronic forensic measures:
The "Rules on Electronic Forensics" clearly specify the case files and documents corresponding to various electronic forensic measures. For instance, according to Articles 10, 12, and 13 of these rules, the implementation “ Seizure and sealing of original storage media ” “鉴”: “ Online extraction of electronic data ” At that time, a record should be prepared (clearly indicating the source, reason, purpose, and recipient of the electronic data, as well as the time, location, method, and process of extraction, along with the reasons why the original storage medium cannot be seized). This record must also include the "List of Extracted and Fixed Electronic Data" (detailing the category, file format, and integrity checksum values, among other details). Other specific requirements are clearly outlined in the relevant provisions, so they will not be listed individually here.
Based on statutory provisions and judicial practice, in addition to expert opinions, case files related to electronic data primarily include the following three categories:
1. Record-type documents. Regardless of the forensic measures taken, the entire process must be meticulously documented in writing, including detailed steps, operational methods, and any necessary screenshots.
2. List-type. List and register the extracted electronic data or seized storage media, ensuring that you clearly note the integrity checksum of the electronic data or the unique identifying features of the storage device (such as its serial number). If photographs are involved, include the accompanying "Image Record Form."
3. Notification-type documents. For measures such as data retrieval and freezing, corresponding notices should be issued, including the "Notice on Assisting in Freezing Electronic Data," the "Notice on Lifting the Freeze of Electronic Data," and the "Notice on Retrieving Evidence," among others. Additionally, if cross-regional evidence collection is involved, a "Letter of Case Collaboration" must also be provided.
The setup of the aforementioned case files is a basic requirement mandated by law, but in specific cases, it still needs to be flexibly assessed and reviewed in light of the actual circumstances.
Measures
|
Applicable Scenarios
|
Relevant case files: Records / List / Notice
|
Seizure, sealing
|
Original storage medium (physical evidence)
Priority options—maximize deductions where applicable.
Encapsulated storage
|
"Seizure Record" "Seizure List"
|
On-site extraction
|
Easily perishable electronic data at the scene
(Memory data, network transmission data, raw storage media difficult to seal for preservation)
|
"Record of On-site Extraction of Electronic Data"
"List of Extracted and Preserved Electronic Data"
|
Online Extraction
|
Electronic data on the internet
|
"Record of Online Extraction of Electronic Data," "Remote Examination Record," "Inventory List for Extracting and Preserving Electronic Data"
|
Remote Inspection
|
To further clarify the situation, network-based remote inspections of the remote computer information system may be conducted when necessary.
|
|
Retrieve
|
Third-party-managed electronic data
|
"Notice of Evidence Collection"
"Evidence Collection List"
"Notice of Assistance in Freezing Electronic Data"
"Notice of Lifting the Freeze on Electronic Data"
"Case Collaboration Letter" (Inter-Regional)
|
Freeze
|
Third-party-managed electronic data
Situations such as large quantities, long extraction times, and difficulties in direct presentation
Disable access permissions—no additions, deletions, or modifications allowed—while granting "read-only" access exclusively to designated personnel.
|
|
Check
|
Methods such as recovery, cracking, statistical analysis, correlation, and comparison
(This is not a specialized issue; on-site investigation and evidence collection efforts naturally continue.)
|
"Record of Electronic Data Examination"
"List of Extracted and Preserved Electronic Data"
|
Investigative Experiment
|
Through experimental methods such as simulation, testing, reconstruction, tracing, and verification, the generation, alteration, destruction, or loss of electronic data—as well as the functionality of software and hardware, their operational mechanisms, and temporary data—can be thoroughly examined and confirmed.
|
"Record of Electronic Data Investigation Experiment"
|
Inspection and Identification
|
Specialized issues that are difficult to determine
|
"Expert Opinion on Forensic Examination"
|
2. How can electronic data be efficiently "examined" or reviewed?
Based on clearly identifying the types of case files related to electronic data, it’s also essential to master efficient methods for reviewing these documents. In practice, the standard approach involves systematically examining each record, checklist, and other relevant materials—tailored to the specific evidence-gathering measures—according to legal requirements. For instance, Article [insert article number] of the "Rules on Electronic Evidence Collection" specifies… 16 To 22 The document provides detailed regulations for on-site evidence collection, emphasizing the need to carefully verify whether the circumstances meet the legal requirement of "unavailability to seize the original storage media," ensuring that operational procedures comply with regulatory standards (e.g., no overwriting allowed, no unauthorized software installation, and full-process video recording). Additionally, it requires that all necessary documentation—such as records, inventories, and witness protocols—be complete, and that integrity check values are fully documented. The same review process applies equally to case files involving other evidence-gathering measures.
However, in practice—especially in cases involving mass-participant cybercrime—the electronic data forensic reports often run into dozens or even hundreds of pages, and there may also be multiple expert opinions. If these documents are reviewed rigidly one by one, it not only leads to inefficiency but also makes it difficult to focus on the core issues. To address this, an integrated "Examination-Data-Collection" approach can be adopted.
The so-called "observe—measure—adopt" refers to:
“鉴”: Refers to the expert opinion. Judicial authorities often rely primarily on the conclusion section of the expert opinion when accepting electronic data as evidence.
"Number": Refers to the electronic data itself—specifically, the concrete data content presented in electronic form.
"Take": Refers to case file materials such as evidence collection records and inventories, as mentioned above.
The process of how the same electronic data flows through litigation roughly involves three stages: "extraction—transfer—expert analysis." The evidence record documents the process of data extraction, with the electronic data itself being the actual object extracted. Meanwhile, the expert opinion relies on this data as the forensic sample. All three elements should align in their respective references. For example, if a company’s server logs involved in a case are stored on Alibaba Cloud’s platform, investigators can remotely examine and extract the data, which is then sent to an expert agency for analysis, ultimately resulting in an expert report. In such cases, the remote examination record, the server log data, and the evidence samples referenced in the expert opinion must all correspond accurately with one another. If any of these steps reveal inconsistencies in descriptions or conflicting details, it could compromise the reliability of the evidence. Therefore, during the review process, the three types of materials—“expert analysis,” “digital data,” and “evidence collection”—can be compared pairwise or cross-referenced collectively. This approach allows investigators to focus on verifying whether the subjects match and whether the details align consistently, ensuring both efficiency and accuracy in identifying potential issues while enabling precise challenges to the evidence.
The above approach can be refined into the following operational steps in practice:
First, systematically organize electronic data using the "identify—quantify—extract" framework.
1. Find the specimen description for the expert opinion. Focusing on expert opinions that influence sentencing and conviction, first clearly identify the evidence materials listed in their introductory sections.
2. Locate the forensic report corresponding to the evidence material. Based on the name, attributes, and other characteristics of the evidence materials, locate the corresponding forensic record. In practice, this step is often the most complex: some materials may not originate from a single record but are instead extracted from multiple records, while others may have no clear matching forensic record at all.
3. No handling of the evidence record found. If the evidence lacks a corresponding record, it can be handled according to Article [insert article number] of the Interpretation of the Criminal Procedure Law. 98 Submit a request to exclude the expert opinion, or apply to the judicial and procuratorial authorities for access to the original data.
Through the above organization, the complex and extensive electronic data in the case can be streamlined into a clear system. For instance, in a certain illegal case involving the unauthorized access to computer information systems, the electronic data was categorized as "Remote Examination Record — Examination Data — 1 "Expert Opinion No." and "Alibaba Cloud Data Retrieval Document — Retrieve Data — 2 "Two systems of expert opinions." For instance, in a case involving the sale and purchase of state-owned assets, the four key pieces of evidence submitted as part of the expert assessments could not be matched to the corresponding collection records. As a result, the defense filed a request with the court to obtain the original electronic data, which effectively served as both cross-examination and a crucial check on procedural fairness.
Second, conduct a similar comparative review of "Identify—Analyze—Adopt."
For the "examination evidence materials" and "evidence collection records" related to the same set of electronic data, a item-by-item comparison should be conducted. Common comparison items typically include: file names, hash values, file sizes, number of files, file paths, file timestamps, and more. If discrepancies are found in the attributes of the same electronic data across different documents in the case file, objections regarding authenticity, relevance, and legality can be raised. Additionally, if the actual electronic data files are accessible (though this is often challenging in practice), you can independently compute their hash values and verify other metadata—such as file names, sizes, timestamps, and paths—before performing a three-way comparison against both the collection records and the expert opinions. For instance, in the previously mentioned case involving the illegal acquisition of computer information system data, 2 The expert opinion pertains to 5 A sample forensic document, but in the corresponding Alibaba Cloud retrieval document, the recorded electronic data is noted. IP The address, quantity, name, size, hash value, and other details all differ from the evidence collected. The defense therefore argued based on this discrepancy: 2 "The evidentiary objection regarding the unidentified source of the forensic sample," and in accordance with Article [insert article number] of the Interpretation of the Criminal Procedure Law. 98 A motion to exclude the expert opinion.
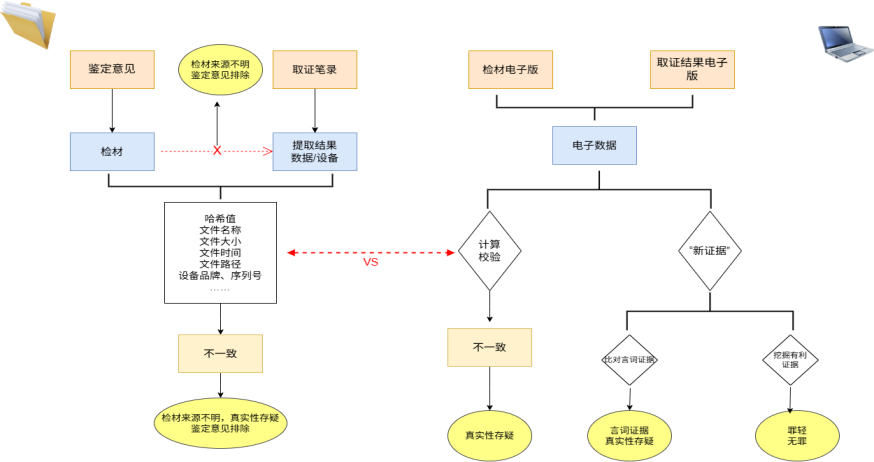
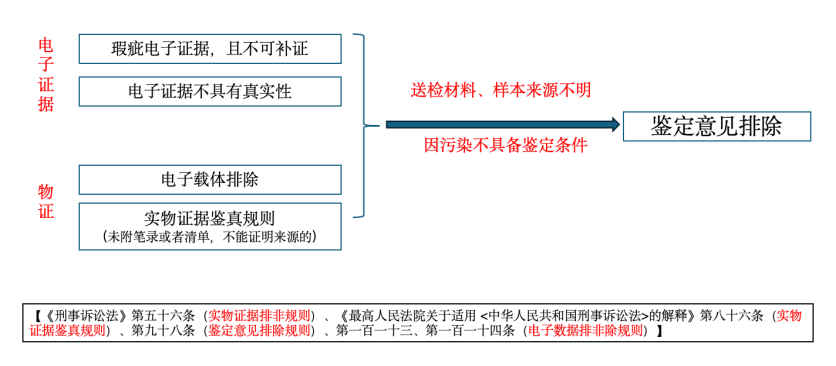
Additionally, given the repeated mention earlier of excluding electronic data examination opinions, we now provide an explanation on the "exclusion" techniques for integrated electronic data. Strictly speaking, the objects of criminal exclusion of illegally obtained evidence do not directly include electronic data; however, existing legal provisions can still be leveraged to achieve the "exclusion" of electronic data from the following three perspectives:
1. Exclude electronic data. Article
2. Exclude electronic carriers. When electronic data is presented in its original storage medium, the storage medium qualifies as physical evidence and is subject to the rules governing physical evidence. In such cases, Article [insert article number] of the Criminal Procedure Law may be invoked. 56 The rules for excluding illegally obtained evidence, as well as Article [number] of the Interpretations of the Criminal Procedure Law 86 Regulations regarding the authentication of physical evidence, namely “ Evidence or documentary evidence whose source cannot be verified due to the absence of a record or inventory shall not be used as the basis for reaching a verdict. ”。
3. Exclude the expert opinion. If any of the aforementioned circumstances involving exclusion of electronic data or storage media exist, an additional request for excluding the expert opinion may be submitted. This is in accordance with Article [insert article number] of the Interpretation of the Criminal Procedure Law. 98 Clauses (iii) and (iv) stipulate that, “ Materials and samples submitted for testing have unclear origins, or are unsuitable for analysis due to contamination. ”, “ Those whose identification objects do not match the submitted materials or samples ” , the expert opinion cannot be used as the basis for final judgment.
III. Techniques for Reviewing Electronic Data
Based on the integrated review approach of "Assess—Analyze—Select," practical applications can also incorporate several specific test-reading techniques, which are summarized below:
1. Similarity Comparison Method
This is an extended method of "compare—quantify—select," particularly useful when multiple expert opinions are available in a case. It involves systematically comparing each item across the different expert assessments to highlight any anomalies in their attributes and details. For instance, in a certain copyright infringement case, four separate expert analyses were conducted sequentially on the same evidence and under the same circumstances. The evidence (a single hard drive) and samples ( U Roll one up) and its key documents ( Excel Legal requirements stipulate that once electronic data is extracted, its integrity must be maintained and it cannot be altered afterward. Therefore, if discrepancies are detected—such as electronic data being modified at a later time than the evidence collection—it raises significant concerns about both its authenticity and完整性. For instance, comparing the data might reveal that a specific file continued to show modification records even days after it was seized, presenting a critical point of contention regarding its reliability. U Although the disk hasn't had its hash value calculated, the number of subfiles, their names, and paths all differ in each inspection. Excel The hash values of the files also differ with each examination. These issues are enough to cast doubt on the authenticity of the electronic data and the reliability of the expert opinions. As a practical step, consider creating a comparative table that lists the characteristics of the evidence files from each examination, clearly highlighting their differences.
2. Screenshot Review Method
Screenshots are an indispensable source of detail in case file materials. Various types of evidence collection records and expert opinions typically include screenshots of each operational step, with some even providing electronic versions of the screenshots. These screenshots can be used to conduct the following reviews:
Step-by-step comparison with screenshots: Verify whether the text description matches the content of the screenshot. For instance, if a certain identification record lists "calculating the hash value" as a step, but the specific date shown in the screenshot for the hash calculation differs—and the calculation took two full days, which is clearly unusual—
Alternative sources for "number": When it’s impossible to obtain the actual electronic data, screenshots often provide crucial information such as the number of files, their names, timestamps, and paths, making them an important basis for review. For instance, in the aforementioned copyright infringement case, although no forensic samples were submitted throughout the litigation, U Disk original carrier, but numerous screenshots fully present it. U The in-court presentation of documents also achieved a good evidentiary effect.
Discovering unusual details: Screenshots often reveal inconsistencies—or even instances of falsification—in transcripts. For example, a certain remote inspection transcript claims to have used U The disk stored the extracted data, but screenshots reveal that a high-capacity portable hard drive was used, and there are clear signs of data being copied into the computer involved in the case.
3. Screen Recording Review Method
Screen recordings can be seen as an extension of screenshot reviews. The "Regulations on Electronic Data" and the "Rules on Electronic Forensics" outline the conditions and requirements for conducting full-process simultaneous recording during online data extraction and remote forensic examinations. When reviewing case files, make sure to check whether the forensic recording files have been submitted, and you can evaluate them from the following perspectives:
Check if the time in the bottom-right corner of the screen recording is correct;
Are there any traces of third-party tools or remote control software appearing in your Favorites, desktop, or taskbar?
Does the login account match the record, and was it indeed provided by the party involved?
Is the downloaded data real-time data or "backup data," and is the backup time reasonable? (This is especially relevant in profit-driven enforcement cases, where it’s common to "preemptively prepare backups" and then directly download the data during evidence collection—issues that can often be uncovered through screen recordings.)
Are there any signs of editing or modifications in the screen recording video?
4. Time Comparison Method
Time review is an intuitive and efficient method, which the author has discussed in detail in other articles. Here, we’ll primarily introduce, using case files as a guide, a straightforward approach that you can start applying right away. Compare the initial collection time of electronic data with the time of its modification.
The initial collection time is usually documented in the forensic record, including specific details such as the dates of seizure and sealing, as well as the timing of online extraction.
Modification times can be checked in bulk via electronic data records, screenshots, or by using simple forensic tools.
Legal requirements mandate that once electronic data is extracted, its integrity must be preserved and it cannot be altered afterward. Therefore, if discrepancies are found—such as electronic data being modified at a later time than the evidence collection—it raises serious doubts about both its authenticity and完整性. For instance, comparing the data might reveal that a particular file continued to show modification records even days after it was seized, providing a critical point of contention regarding its credibility.
Summary:
Electronic evidence, as the most common yet also the most complex type of evidence encountered in modern case handling, holds review value that extends far beyond its role in “ The data itself ” The verification is further reflected in the thorough analysis of relevant case-file materials. From identifying the specific types of case files corresponding to electronic data, to applying “ Mirror — Numbers — Take ” An integrated approach, combined with mastering specific techniques such as analogy comparison, screenshot review, screen recording analysis, and time alignment, can help legal professionals go beyond surface-level records, uncover hidden issues, and present compelling cross-examination arguments. In practice, reviewing case files should not be merely a formality—it should instead serve as a critical preliminary step and a key entry point for effective cross-examination. 。
Author: Wang Ran, Associate Professor at the School of Discipline Inspection and Supervision, Renmin University of China.
Source: Criminal Defense Research Center, China University of Political Science and Law
Beijing Headquarters Address: Floor 17, East Section, China Resources Building, No. 8 Jianguomen North Avenue, Dongcheng District, Beijing
Wuhan Branch Office Address: Room 1001, 10th Floor, Huangpu International Center, Jiang'an District, Wuhan City, Hubei Province
Layout: Wang Xin
Review: Management Committee

Related News


